LSA 4: Identify Trusts¶
Trusts¶
In Active Directory (AD), trusts are essential relationships between domains, trees, and forests that enable resource access across different parts of the AD infrastructure. Trusts are fundamental for managing security, permissions, and authentication across multiple domains or forests, especially in large or multi-forest environments.
There are two primary types of trust relationships in AD: Transitive Trusts and Non-Transitive Trusts. Each type serves different purposes and has specific characteristics.
1. Transitive Trusts¶
-
Definition: A Transitive Trust is a two-way trust relationship where if Domain A trusts Domain B, and Domain B trusts Domain C, then Domain A will automatically trust Domain C. This type of trust allows access to resources across multiple domains without needing to manually establish trust relationships between every pair of domains.
-
Key Characteristics:
- Two-Way Relationship: Transitive trusts automatically create mutual trust, meaning both domains in the relationship can access each other's resources.
- Automatic Inheritance: The trust extends across all domains in the hierarchy. For example, if Domain A trusts Domain B, and Domain B trusts Domain C, then Domain A also trusts Domain C by transitivity.
-
Simplified Administration: Transitive trusts reduce administrative overhead by ensuring that trust relationships flow naturally between all connected domains.
-
Use Cases: Transitive trusts are commonly used within a single AD forest, where multiple domains may need to share resources without complex trust setups.
2. Non-Transitive Trusts¶
-
Definition: A Non-Transitive Trust is a one-way trust that requires explicit configuration. If Domain A trusts Domain B, users in Domain A can access resources in Domain B, but the reverse is not true unless a separate trust is explicitly created between Domain B and Domain A.
-
Key Characteristics:
- One-Way Relationship: Non-transitive trusts are one-way, meaning only the trusting domain (Domain A) can access resources in the trusted domain (Domain B). The reverse is not true unless manually configured.
- Manual Setup: These trusts must be manually configured by an administrator. Unlike transitive trusts, non-transitive trusts do not automatically propagate.
-
Security Implications: Non-transitive trusts offer more control over resource access and can be used in cases where an organization wants to restrict access in one direction.
-
Use Cases: Non-transitive trusts are often used in cases where a domain wants to grant access to resources to another domain, but does not want to automatically grant reverse access.
3. Types of Trusts in Active Directory¶
Active Directory supports several types of trust relationships that serve different purposes, including:
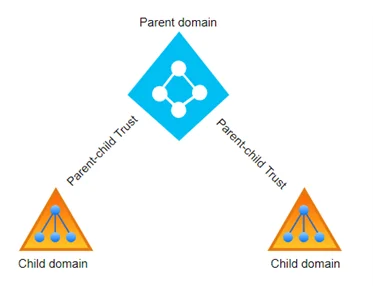
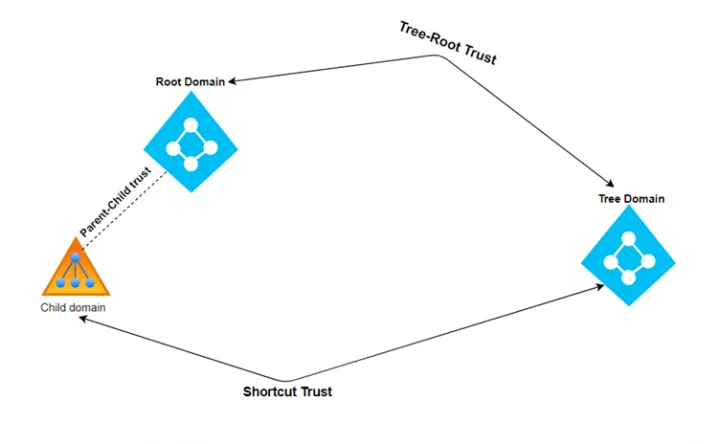
Parent-Child Trusts¶
-
Definition: A Parent-Child Trust is a two-way transitive trust that is automatically created when a new child domain is added to a parent domain. This relationship ensures that all child domains within the same AD tree can access resources in the parent domain, and vice versa.
-
Key Characteristics:
- Implicit Creation: The trust is established automatically when a child domain is created, without requiring manual configuration.
-
Transitive: Parent-child trusts are inherently transitive, meaning that the trust extends throughout the domain tree, providing access to all child and parent domains.
-
Example: If a parent domain
company.comhas a child domainsales.company.com, both domains can access resources in each other’s namespace.
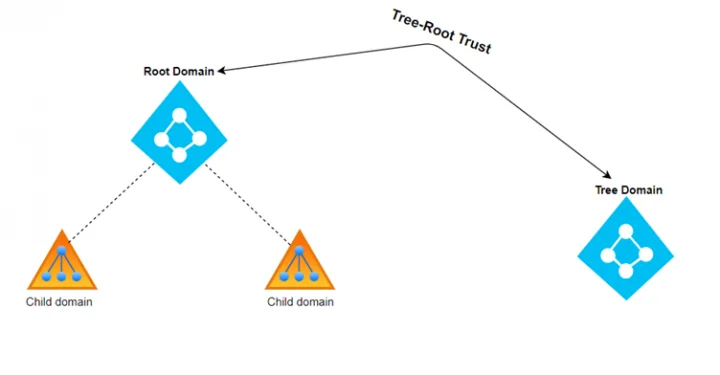
Tree-Root Trusts¶
-
Definition: A Tree-Root Trust is also a two-way transitive trust that is created when a new domain tree is added within a forest. Like parent-child trusts, tree-root trusts enable mutual access to resources across multiple domain trees within the same forest.
-
Key Characteristics:
- Automatic Creation: Tree-root trusts are automatically established between the new tree and existing trees in the forest.
-
Transitive Trust: This is a transitive trust, allowing automatic resource access between multiple domain trees.
-
Example: If the
company.comdomain tree is part of a forest, and a new domain treeexample.comis added, a tree-root trust allows both domains to share resources.
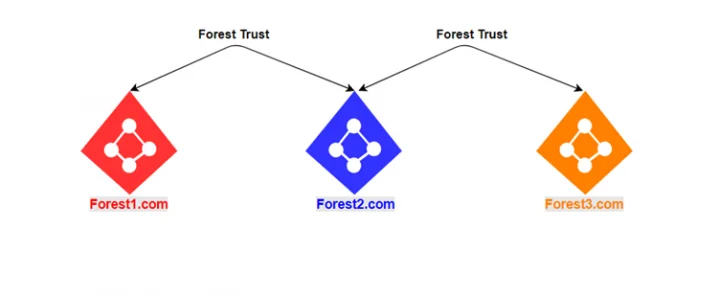
Forest Trusts¶
-
Definition: A Forest Trust is a transitive trust between two Active Directory forests. It can be either one-way or two-way, and it enables the sharing of resources across multiple forests.
-
Key Characteristics:
- Explicit Configuration: Forest trusts must be manually established between the root domains of two different forests.
- Transitive: A forest trust allows trust relationships to propagate throughout the forest, but it does not extend to other forests unless explicitly set up.
-
DNS Resolution: A forest trust requires proper DNS resolution between forests to ensure that both can locate resources across trust boundaries.
-
Example: Forest A (
company.com) can establish a forest trust with Forest B (example.com), enabling users from one forest to access resources in the other forest.
Realm Trusts¶
-
Definition: A Realm Trust allows trust relationships between an AD domain or forest and non-AD systems, such as a Kerberos v5 realm (commonly found in UNIX or Linux systems). Realm trusts are useful for enabling cross-platform interoperability and providing access between AD and non-Windows systems.
-
Key Characteristics:
- Cross-Platform: Realm trusts facilitate authentication and resource access between Windows and non-Windows systems.
-
One-Way or Two-Way: These trusts can be either one-way or two-way, depending on the configuration.
-
Use Cases: Realm trusts are often used when integrating Active Directory with other identity management systems such as those found in UNIX or Linux environments.
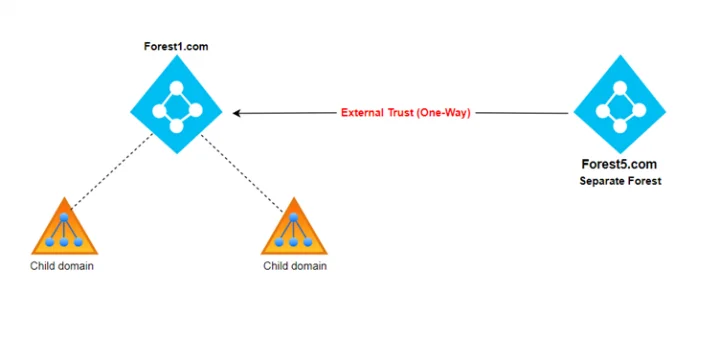
External Trusts¶
-
Definition: External Trusts are one-way non-transitive trusts that are established between an AD domain and an external domain outside the AD forest. These are manually configured and often used to provide access to resources from external domains.
-
Key Characteristics:
- Manual Configuration: External trusts require manual creation by administrators and are often used in scenarios involving external partners or non-AD systems.
-
One-Way: Typically, these trusts are one-way, meaning one domain trusts the other but not vice versa.
-
Example: A domain
company.commight establish an external trust with a third-party domainpartner.comto grant resource access.
Shortcut Trusts¶
-
Definition: Shortcut Trusts are manually created, one-way transitive trusts within a forest, designed to optimize the authentication process by bypassing the default hierarchy of parent-child and tree-root trusts.
-
Key Characteristics:
- One-Way: These trusts are typically one-way, and are used to streamline the authentication process between two domains that are far apart in the trust hierarchy.
-
Improved Performance: Shortcut trusts reduce the number of hops needed for authentication, improving access times for users in domains that are not directly connected in the hierarchy.
-
Use Cases: Shortcut trusts are typically used when a domain frequently accesses resources in another domain, and administrators want to reduce the complexity of authentication paths.
Key Takeaways¶
- Transitive Trusts: Enable automatic, two-way relationships between domains or forests, simplifying resource sharing and authentication across multiple domains.
- Non-Transitive Trusts: Provide one-way relationships, offering more control over which domains have access to resources.
- Multiple Trust Types: Different trust types (parent-child, tree-root, forest, external, realm) offer flexibility to accommodate various organizational and security needs.
- Trusts and Security: Trusts must be carefully configured to ensure that access to resources is properly managed and that security policies are adhered to. Misconfigurations can lead to unauthorized access or vulnerabilities across domain boundaries.