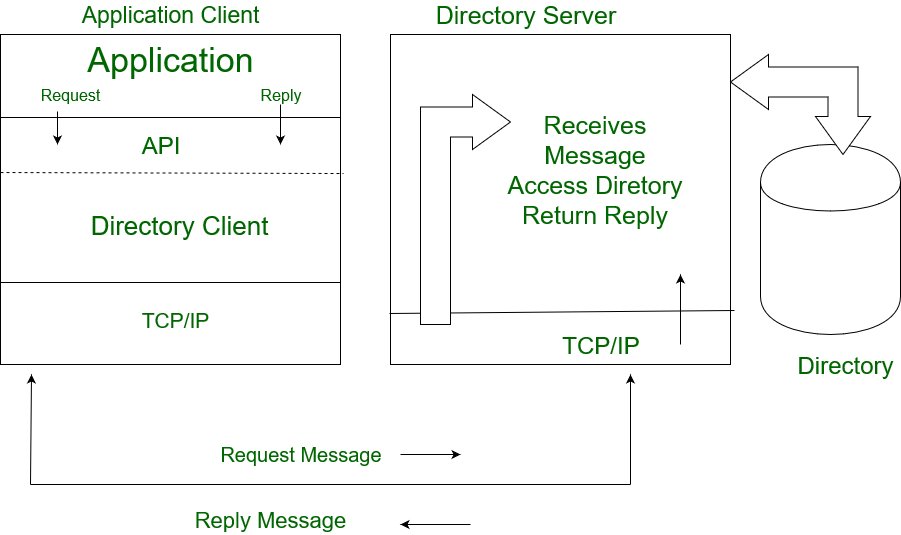
LSA 1: Describe LDAP Models¶
LDAP (Lightweight Directory Access Protocol) is a software protocol designed for accessing and managing directory services over a network. It enables the retrieval of directory data, such as information about individuals, organizations, network resources, and devices, whether hosted on the public internet or a corporate intranet.
LDAP is referred to as "lightweight" because it is a simplified version of the more complex Directory Access Protocol (DAP), which is part of the X.500 standard for directory services. The "lightweight" designation comes from LDAP’s reduced resource and processing requirements, making it faster and less resource-intensive compared to its predecessor.
One of the most common uses of LDAP is for centralized authentication. It integrates with various applications and services to authenticate users and control access to resources based on data stored in a central directory. By using LDAP, a single authentication can grant users access to multiple services, a concept known as Single Sign-On (SSO). LDAP is typically used as a plug-in or an extension for applications, simplifying user authentication by querying a central directory for credentials and other essential data.
Key Features of LDAP:¶
- Standardized Protocol: LDAP is an open, vendor-neutral standard, making it widely adopted for directory services across different platforms.
- Centralized Directory Access: It allows efficient querying and modification of directory data, such as user credentials, resource availability, and organizational structures.
- Interoperability: LDAP supports cross-platform integration, enabling different operating systems (Windows, Linux, macOS) to communicate and share directory information.
LDAP Models¶
LDAP operates based on four fundamental models that guide how information is structured, accessed, modified, and protected in the directory service. These models define the behavior of the protocol and ensure that it functions properly across various implementations and use cases.
1. Information Model¶
The Information Model defines the structure of the data stored in an LDAP directory. Information is stored as entries, which represent real-world objects such as: - People (e.g., John Doe) - Resources (e.g., printers, files, or servers) - Organizations (e.g., departments or divisions)
Each entry is composed of a set of attributes, which provide specific details about the object. For example, a user entry may have attributes like firstName, lastName, email, and phoneNumber. Each attribute has a defined syntax that dictates what kind of data can be stored in that attribute (e.g., a string, a date, etc.).
2. Naming Model¶
The Naming Model explains how entries are organized and identified within the LDAP directory. Entries are arranged in a hierarchical, tree-like structure known as the Directory Information Tree (DIT). This tree allows for logical grouping and identification of objects.
Each entry in the DIT is uniquely identified by a Distinguished Name (DN), which is a string that uniquely identifies an object within the directory. The DN is composed of multiple Relative Distinguished Names (RDNs) that describe the location of the entry within the directory hierarchy. The DN ensures that each object can be accessed quickly and accurately.
3. Functional Model¶
The Functional Model defines the operations that LDAP supports for interacting with directory data. LDAP provides several key operations for managing and querying directory entries: - Query: Search for entries in the directory based on specific criteria (e.g., find all users in a particular department). - Update: Modify, add, or delete entries in the directory (e.g., update a user's email address or add a new user). - Authenticate: Verify the identity of users or services based on their credentials stored in the directory.
These operations allow administrators and applications to interact with the directory and perform necessary tasks such as adding users, updating attributes, or checking if a user is authorized.
4. Security Model¶
The Security Model in LDAP governs how directory information can be protected from unauthorized access or modification. It ensures that sensitive data is kept secure while enabling proper access controls. The BIND operation is a key aspect of this model. BIND is the process used to authenticate users to the directory. Depending on the level of security required, several bind methods can be used, including: - Simple Bind: A straightforward method where the client sends the username and password to authenticate. - SASL Bind: A more secure authentication method that supports various mechanisms, such as certificates or Kerberos, for stronger security.
LDAP directories can also enforce access controls, ensuring that only authorized users can access or modify certain data based on their roles and permissions.
LDAP Ports¶
- Port 389: This is the default port for non-secure LDAP communication, typically used for unencrypted LDAP traffic.
- Port 636: This port is used for Secure LDAP (LDAPS), which encrypts traffic using SSL/TLS, providing an additional layer of security when transmitting sensitive information, such as passwords.
LDAP and Active Directory¶
While LDAP and Active Directory (AD) are closely related, they are not the same thing. However, LDAP plays a crucial role in how Active Directory functions.
LDAP’s Role in Active Directory (AD):¶
- Directory Protocol: LDAP is the protocol used by Active Directory to allow clients to access and manage information stored within the AD database. In other words, Active Directory relies on LDAP as its primary communication protocol for handling directory requests.
- Authentication: LDAP is often used for authentication within AD. When a user logs into a Windows network, AD uses LDAP to verify the user’s credentials stored in the directory.
Cross-Platform Compatibility:¶
-
LDAP is a cross-platform protocol, meaning that it can be used on various operating systems, including Windows, Linux, macOS, and more. This flexibility allows for the interoperability of different directory services across a network. For example, LDAP enables communication between Microsoft Active Directory and OpenLDAP, Apache Directory Server, Apple Open Directory, and other directory services.
-
Active Directory, while primarily used in Windows-based environments, must use LDAP to connect with other directory services in a cross-platform network. Without LDAP, Active Directory could not exchange information with non-Microsoft directory systems, which is essential for enterprise environments with diverse platforms.
Key Difference Between LDAP and AD:¶
- Active Directory (AD) is a directory service that stores information about network objects such as users, computers, and resources. It is a Microsoft proprietary service used for managing permissions and security within a Windows-based network.
- LDAP, on the other hand, is a protocol that allows access to the directory data stored in systems like Active Directory. It acts as the language that enables querying and updating data in directories.
LDAP is the protocol, and Active Directory is the directory service that uses LDAP to facilitate access to its stored data and authentication services.
Summary¶
LDAP is an essential protocol for directory services that provides a lightweight and efficient way to store and access data across a network. Whether used in Active Directory or other directory services, LDAP helps organizations centralize authentication, manage users and resources, and support cross-platform interoperability. Understanding LDAP’s role, structure, and security models is critical for IT administrators managing enterprise networks and services.